
Information Security and Cryptography
Home
About Us
People
Teaching
Research
Publications
Awards
Links
Contact
Internal
Information security and cryptography play a major role in the digital age. Images as confidential information constitute a special type of messages. On one hand this allows adapted attacks, that cannot be applied to conventional text messages. On the other hand it opens the door to novel cryptographic applications. In both cases a broad knowledge in the area of image processing is of major importance.
Information Security
Reflecting objects such as tea pots and glasses, but also the user's eye and diffusely reflecting objects such as a user's shirt, can be used to spy on confidential data displayed on a monitor. However, the ability to read this information is often limited by blur. In [1] we show how (non-blind) deconvolution techniques can be used to remove motion blur and out-of-focus blur so that the image quality is drastically improved.
 Reflections captured in the eye from a distance of 10 meters. |
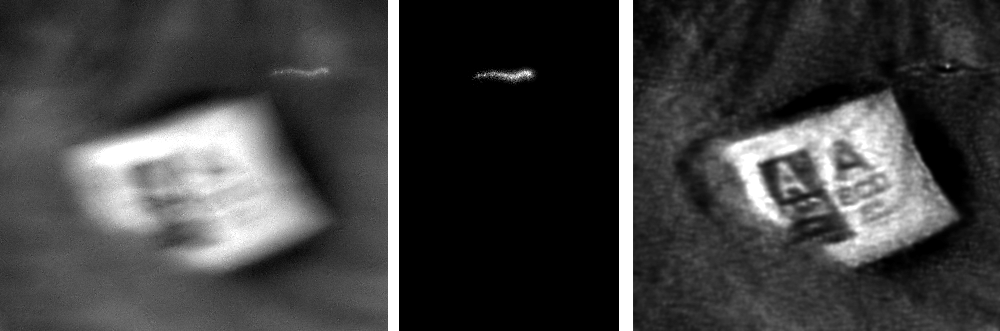 Example of an extremely blurred image (in the eye, from 10 meters) with PSF captured at the same time (left), the extracted PSF (middle), and the result of deconvolution (right). |
Steganography
Steganography is the art of hiding the presence of an embedded message (called secret) within a seemingly harmless message (called cover). It can be seen as the complement of cryptography, whose goal is to hide the content of a message. In [2] we demonstrate that one can adapt our diffusion-based image compression techniques such that they become ideally suited for steganographic applications. The resulting method, which we call Stenography with Diffusion Inpainting (SDI), even allows to embed large colour images into small grayscale images. Moreover, our approach is well-suited for uncensoring applications. A web demonstrator for hiding as well as one for censoring is available at http://stego.mia.uni-saarland.de.
 Cover image |
 Stego image, i.e. cover containing a secret. |
-
M. Backes, T. Chen, M. Dürmuth, H. Lensch, M. Welk:
Tempest in a teapot: compromising reflections revisited.
Proc. 30th IEEE Symposium on Security and Privacy, Oakland, USA, 315–327. IEEE Computer Society, 2009. -
M. Mainberger, C. Schmaltz, M. Berg, J. Weickert, M. Backes:
Diffusion-based image compression in steganography.
In G. Bebis, R. Boyle, B. Parvin, D. Koracin, C. Fowlkes, S. Wang, M.-H. Choi, S. Mantler, J. Schulze, D. Acevedo, K. Mueller, M. Papka (Eds.): Advances in Visual Computing, Part II. Lecture Notes in Computer Science, Vol. 7432, 219-228, Springer, Berlin, 2012.
MIA Group
©2001-2023
The author is not
responsible for
the content of
external pages.
Imprint -
Data protection